Network Policy Demo¶
Official documentation: About network policy
I presented this demo at the Next Generation Datacenter webinar, here the recording (in German)
Environment¶
Deploy Environment¶
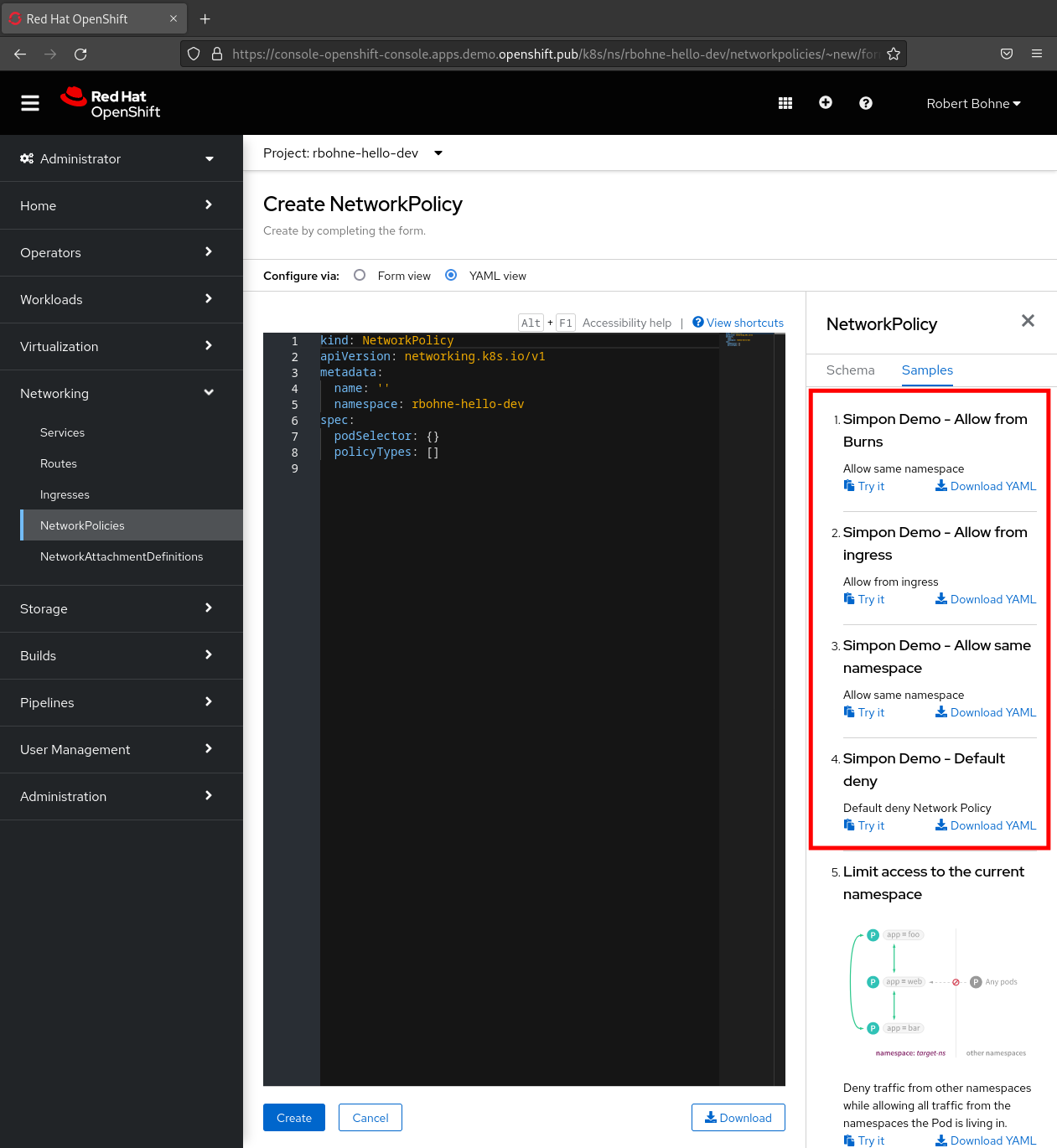
Optional: Deploy OpenShift Console samples¶
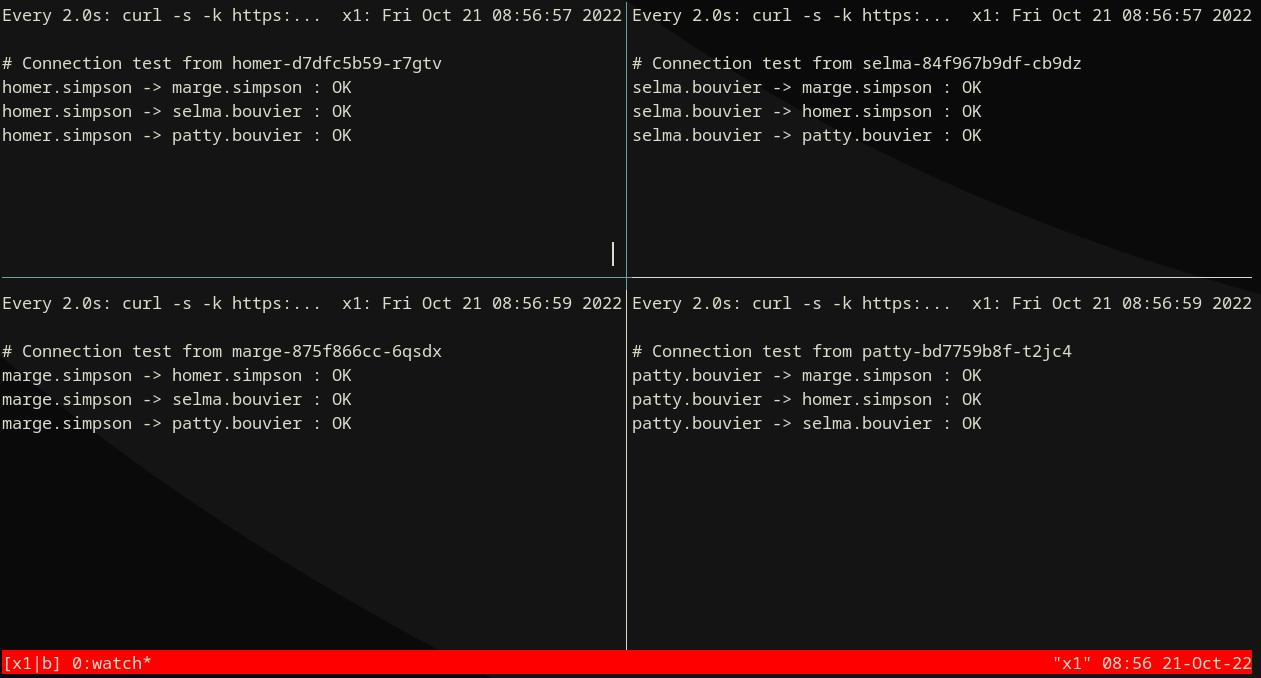
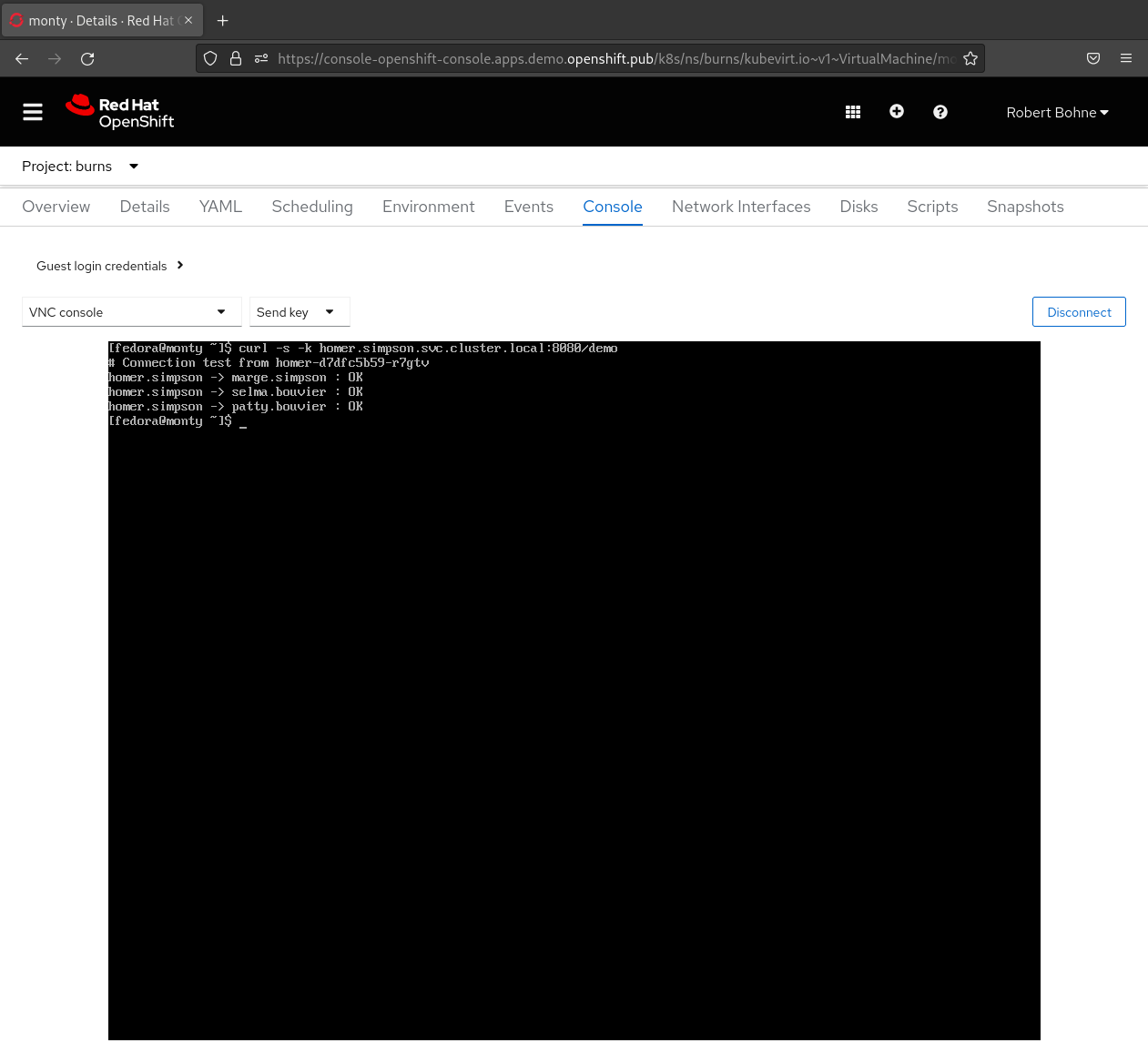
Start Monitor¶
Option 1) Local tmux script¶
Option 2) via Pod¶
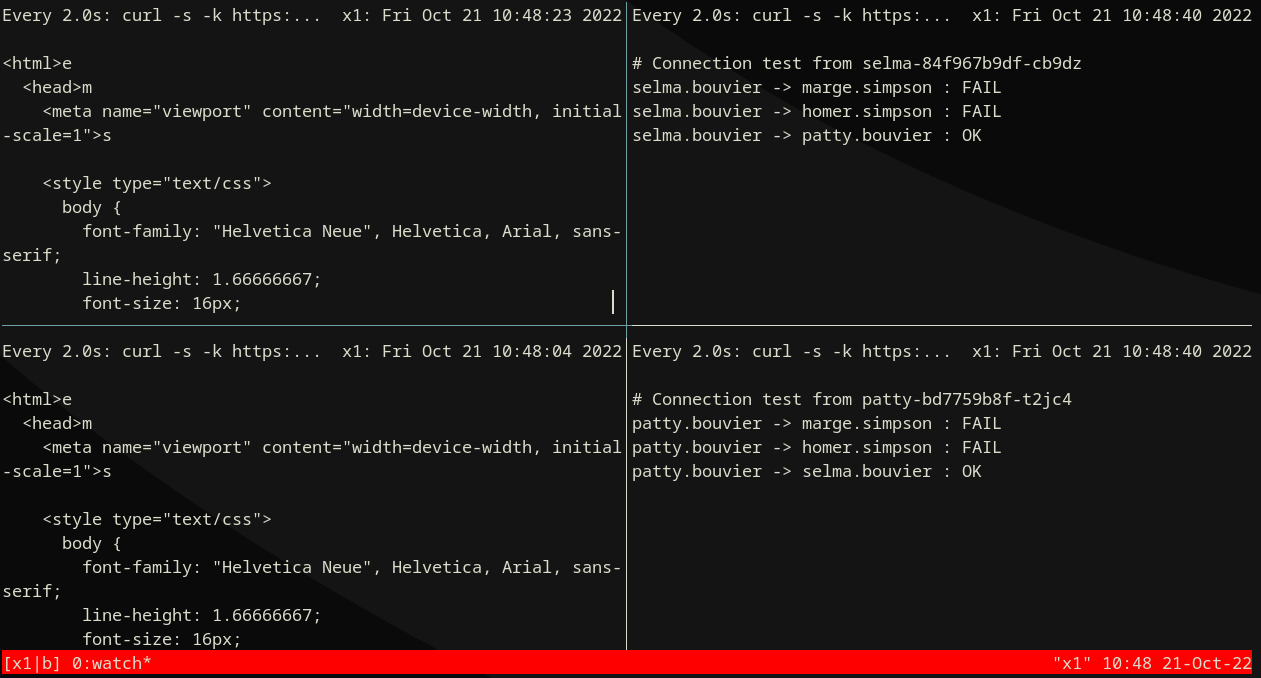
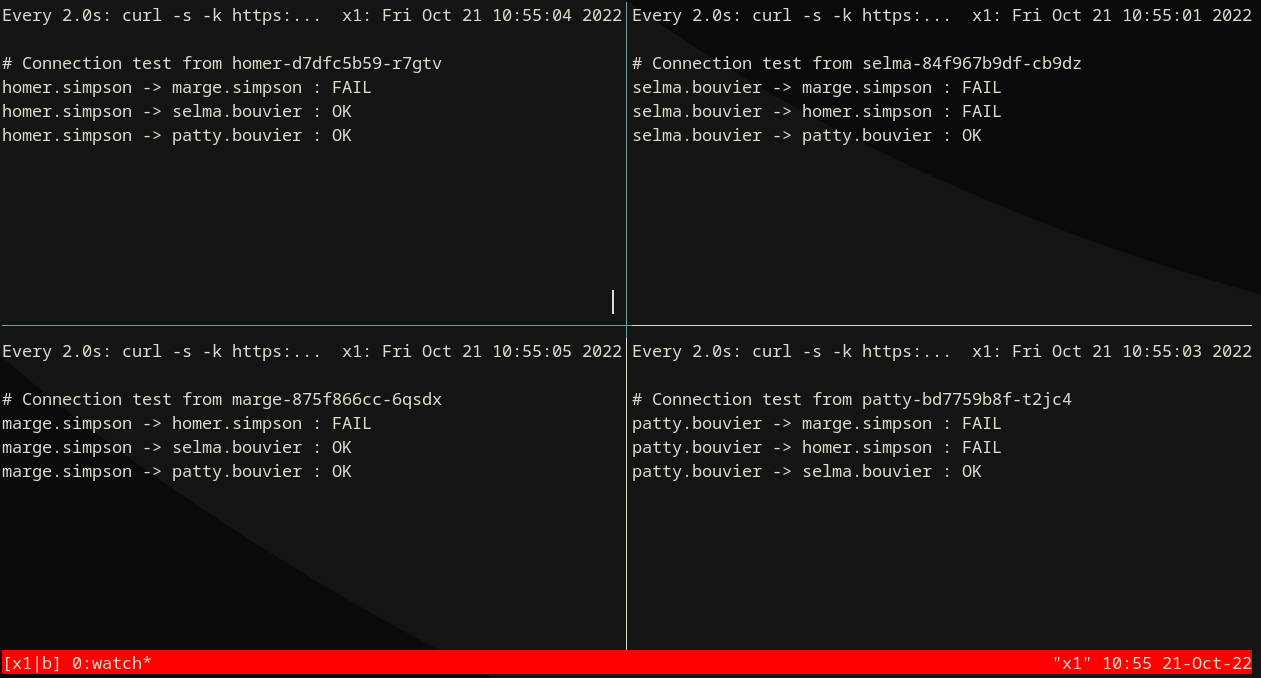
Watch logs:
Step 1) Default deny¶
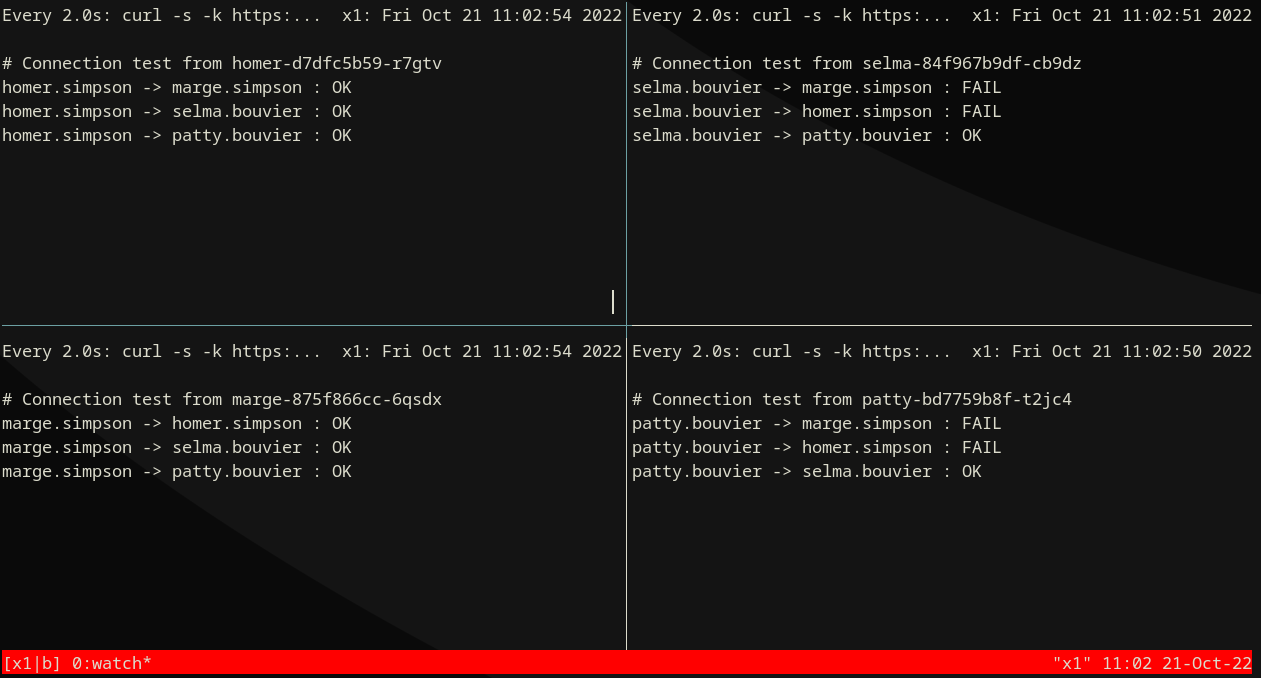
Step 2) Allow ingress¶
Step 3) Allow ingress¶
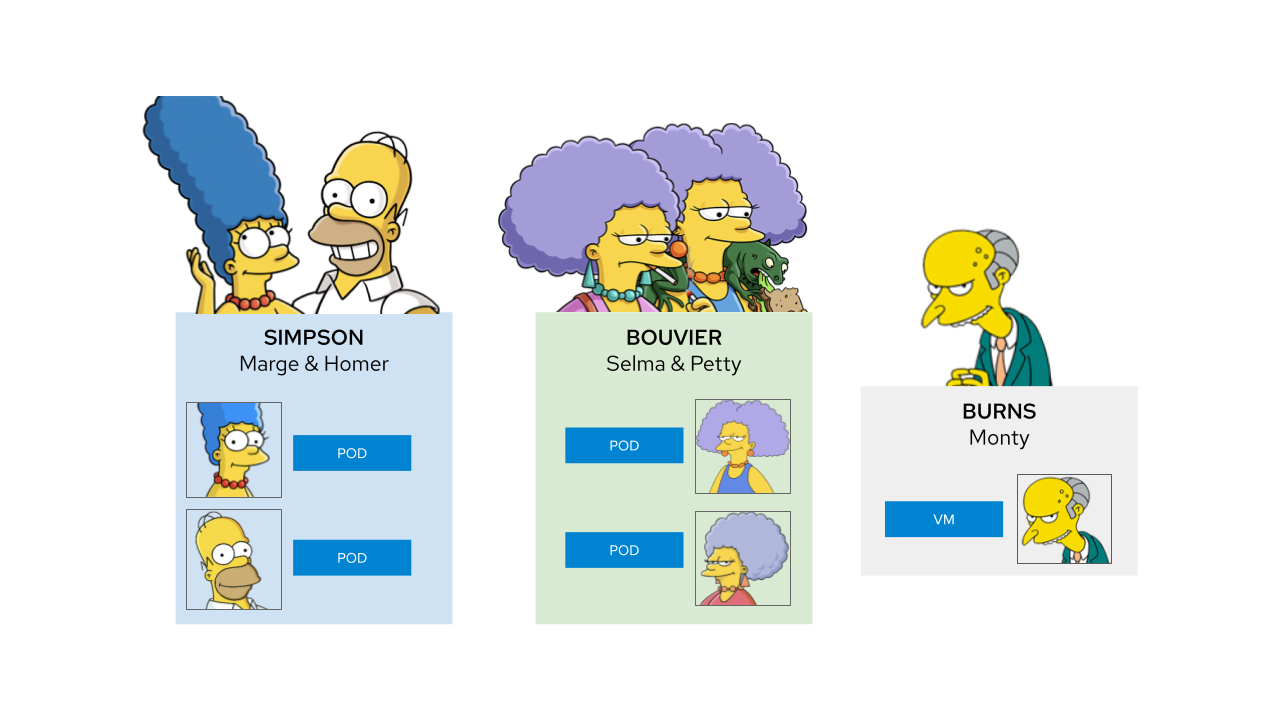
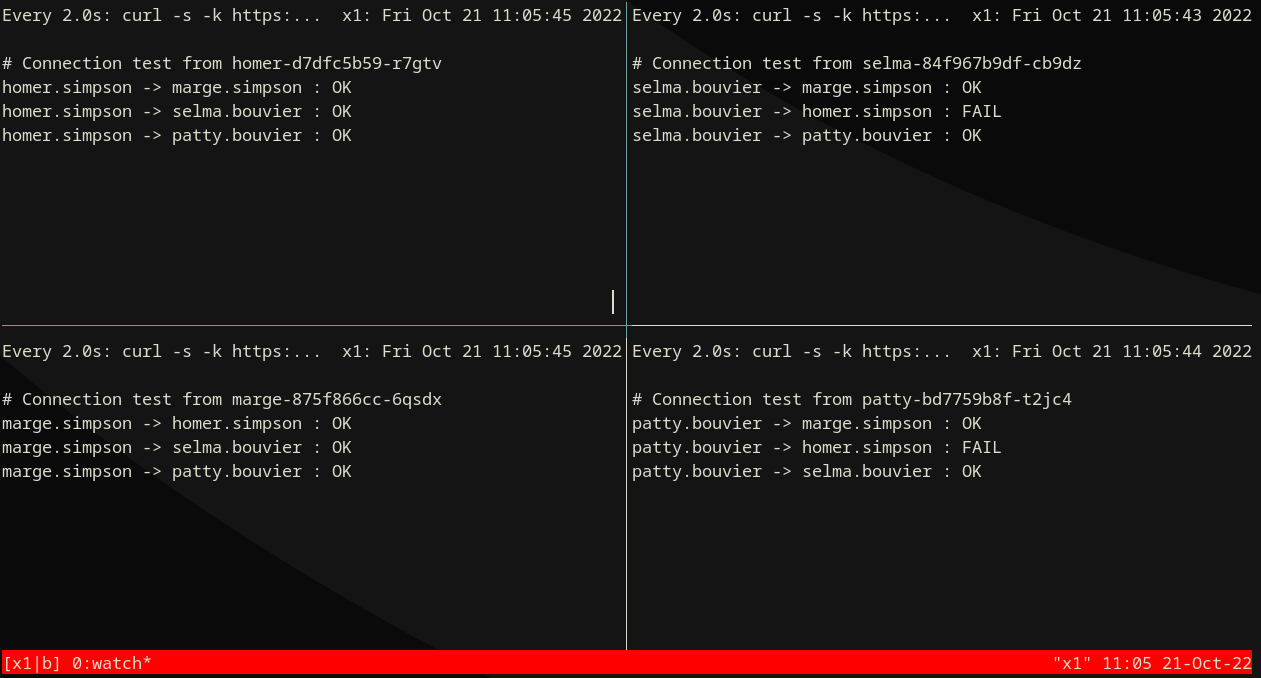
Step 4) Allow from Bouviers to Marge Simpson¶
Step 5) Allow from Burns to Simpson¶
2023-12-15
2022-10-18