External DNS with FreeIPA (RFC2136)
Sadly the External DNS Operator do not support RFC2136. Let's use the upstream one.
Thanks to astrid for the starting point.
Prepare IPA DNS Zone
Generate a TSIG key and register it
| dnssec-keygen -a HMAC-SHA512 -b 512 -n HOST openshift-external-dns
|
| $ cat Kopenshift-external-dns.+165+16478.private
Private-key-format: v1.3
Algorithm: 165 (HMAC_SHA512)
Key: c3LyD11u....xX6WA==
Bits: AAA=
Created: 20240205134832
Publish: 20240205134832
Activate: 20240205134832
|
| $ cat /etc/named/ipa-ext.conf
...
key "openshift-external-dns" {
algorithm hmac-sha512;
secret "c3LyD11u....xX6WA==";
};
|
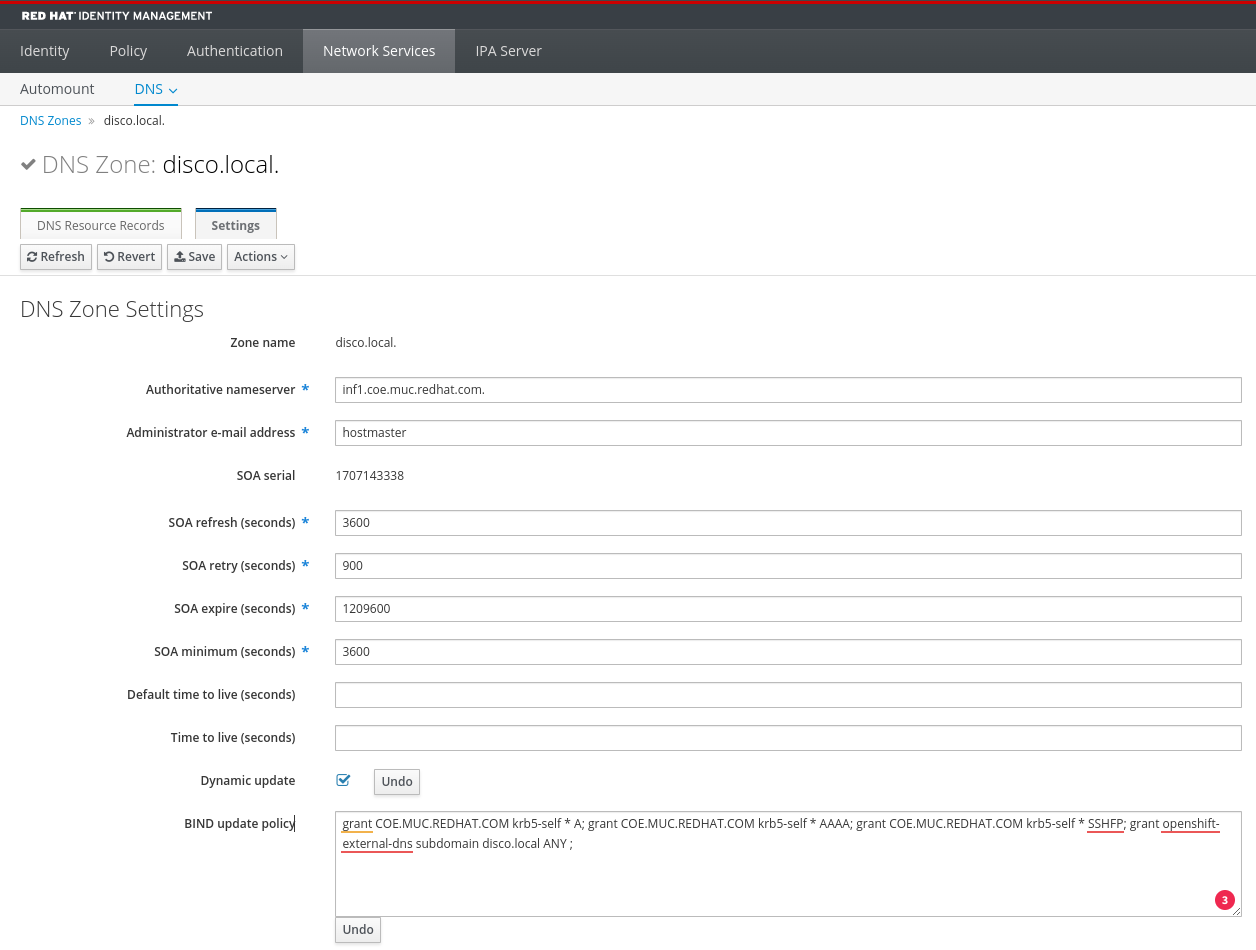
Allow DNS updates and zone transfer for the key
Select the zone you want to manage, in my example .disco.local:
- Enable
Dynamic update
- Add
grant openshift-external-dns subdomain disco.local ANY ; to BIND update policy
Details about the policy configuration you can here
Deploy External DNS
based on Configuring RFC2136 provider
Deployment
Create a secret with the tsig key c3LyD11u....xX6WA==
| oc create secret generic external-dns-rfc2136-tsig-secret \
--from-literal=EXTERNAL_DNS_RFC2136_TSIG_SECRET="c3LyD11u....xX6WA=="
|
Check the logs of the external-dns pod
| oc logs -n infra-external-dns deployment/external-dns
|
Example deployment
- Required MetalLB or support of service type LoadBalancer.
| oc new-project external-dns-demo
oc apply -f https://examples.openshift.pub/cluster-configuration/external-dns/../../deploy/deployment-simple-nginx.yaml
oc patch service/simple-nginx --type merge -p '{"spec":{"type":"LoadBalancer"}}'
oc annotate service/simple-nginx external-dns.alpha.kubernetes.io/hostname='external-dns-demo.disco.local'
oc annotate service/simple-nginx external-dns.alpha.kubernetes.io/ttl='60'
|
2024-02-06
2024-02-05
Contributors:

