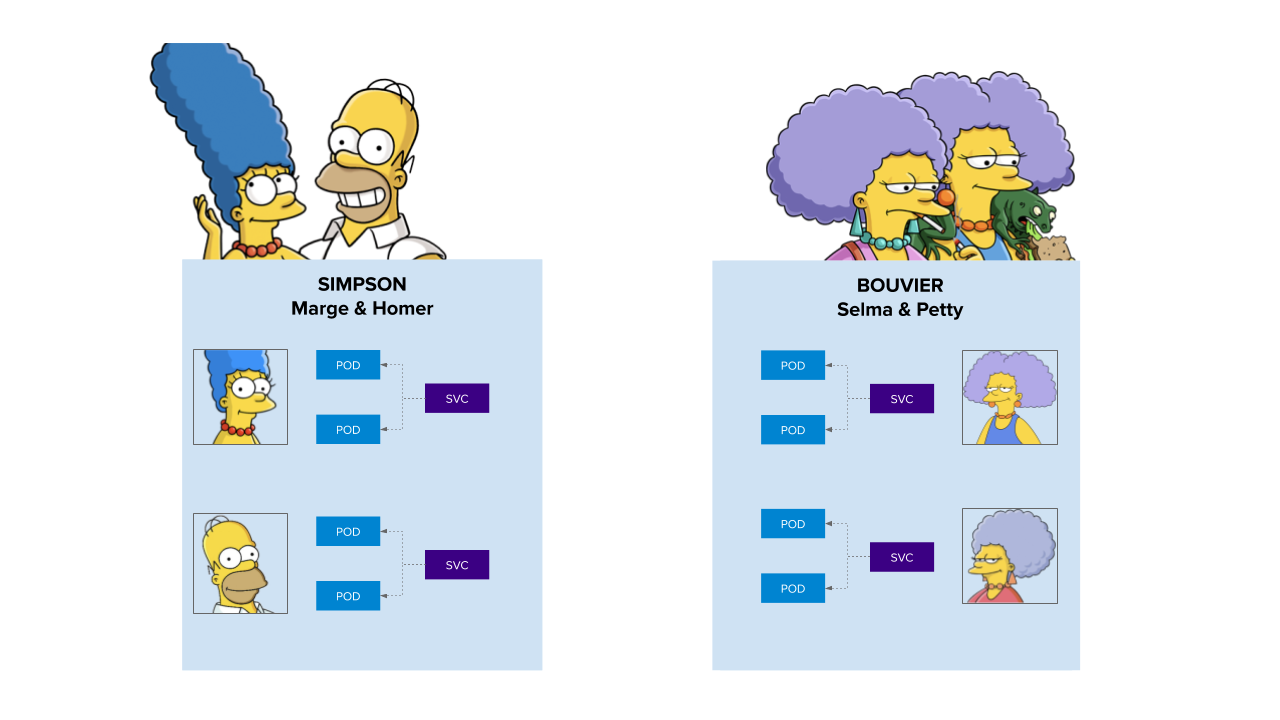
Network Policy with OVNKubernetes¶
Info
Work in progress not ready yet!
Nice to know / Basics¶
- Based on labeling or annotations
- project / namespaces seldom have labels :-/
- Empty label selector match all
- Rules for allowing
- Ingress -> who can connect to this POD
- Egress -> where can this POD connect to
- Rules
- traffic is allowed unless a Network Policy selecting the POD
- traffic is denied if pod is selected in policie but none of them have any rules allowing it
- = You can only write rules that allow traffic!
- Scope: Namespace
Tutorial / Demo - OpenShift v4!¶
Deploy demo environment¶
Download some helper scripts¶
Run connection overview¶
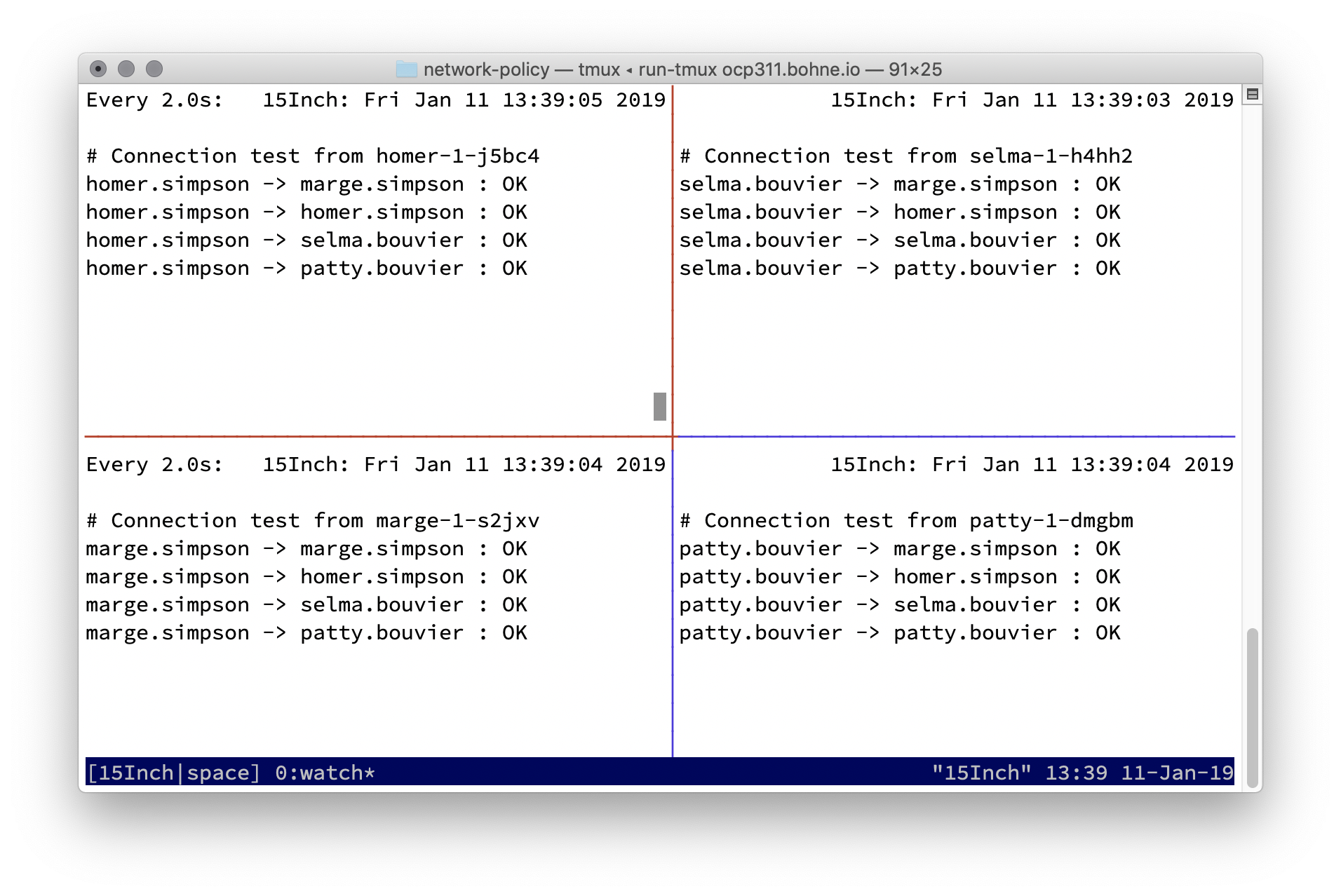
Discover the environment¶
List POD's¶
Let's start with the Network Policy demonstration¶
Every one can connect to each other
Case 1 - Simpson - default-deny¶
Diff of OpenFlow13
2) Simpson allow from openshift-ingress namespaces, because of router¶
Because of HostNetwork access of the OpenShift Ingress you have to apply a label to the default namespace:
Diff:
Warning
Problem - did not work! Bug 1909777 - Setting up multitenant netwotk policy does not work with OVN-Kubernetes network plugin.
3) Simpson allow internal communcation¶
Diff
4) Selma and Patty want's to talk with Marge!¶
1) First label the namespace bouvier:
2) Apply Network Policy
Diff
Nothing??
Destroy demo env¶
Useful commands¶
| Info | Command |
|---|---|
| Dump northbound db | oc rsh -n openshift-ovn-kubernetes -c northd ovnkube-master-6s6bw ovn-nbctl -C /ovn-ca/ca-bundle.crt -p /ovn-cert/tls.key -c /ovn-cert/tls.crt --db=ssl:192.168.51.10:9641 --pretty show |